Quiz
Executives have asked for an organizational risk assessment. The security officer is given a list of all
assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose
two.)
Quiz
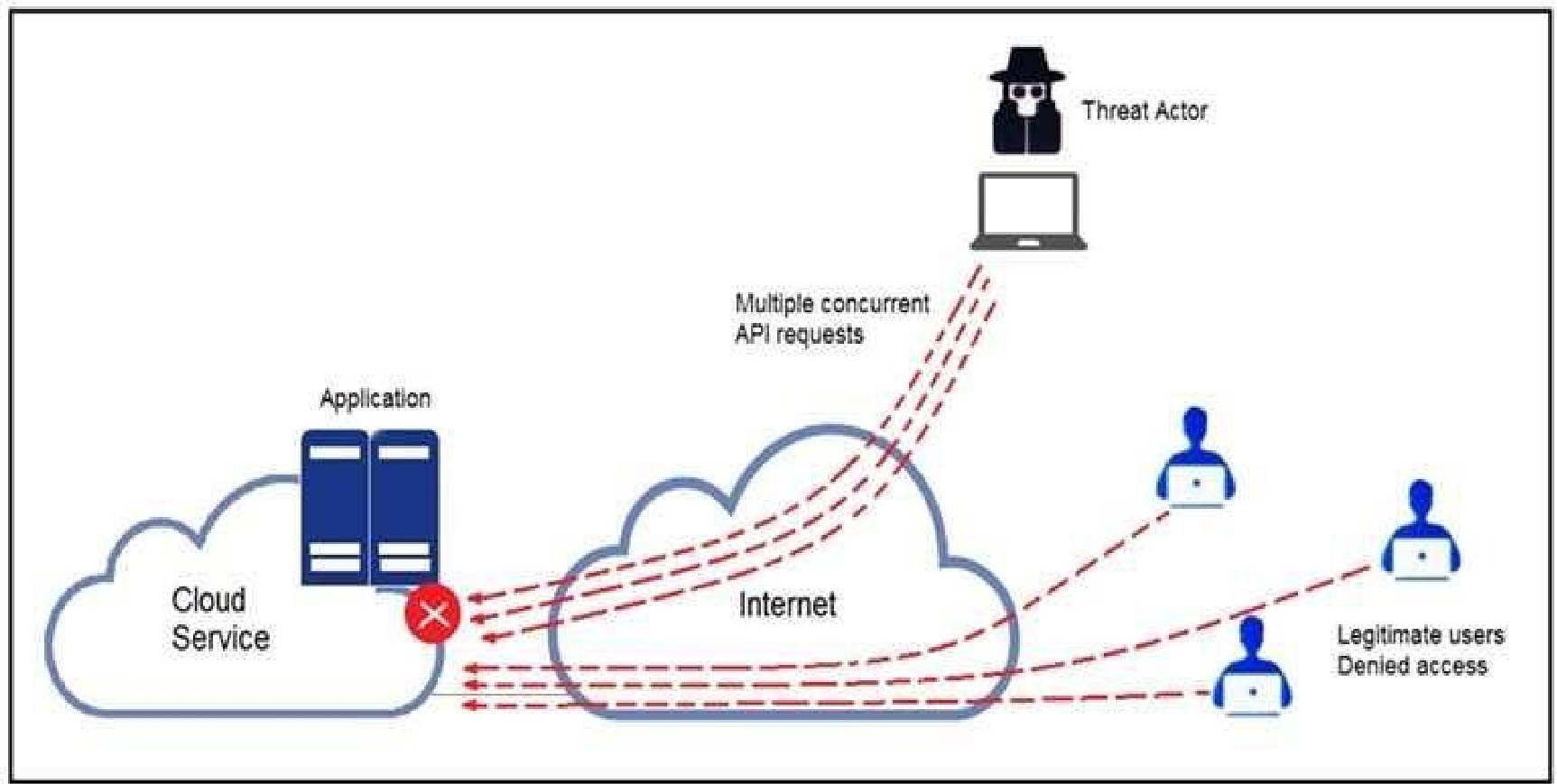
A threat actor behind a single computer exploited a cloud-based application by sending multiple
concurrent API requests. These requests made the application unresponsive. Which solution protects
the application from being overloaded and ensures more equitable application access across the
end-user community?
Quiz
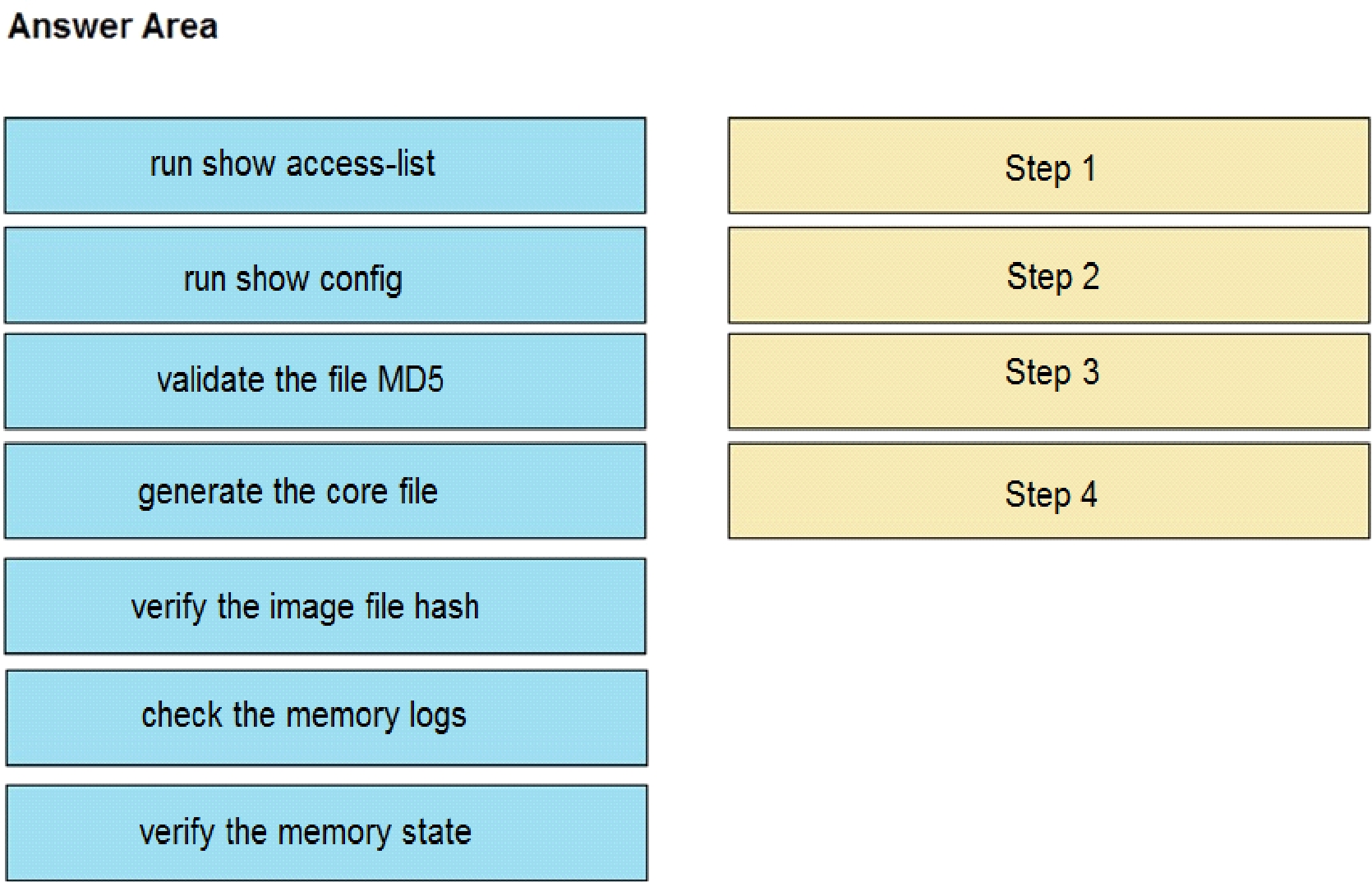
An organization lost connectivity to critical servers, and users cannot access business applications
and internal websites. An engineer checks the network devices to investigate the outage and
determines that all devices are functioning. Drag and drop the steps from the left into the sequence
on the right to continue investigating this issue. Not all options are used.
Quiz
thirty-minute timeframe, stole the password for the administrator account and attempted to access
3 company servers. The threat actor successfully accessed the first server that contained sales data,
but no files were downloaded. A second server was also accessed that contained marketing
information and 11 files were downloaded. When the threat actor accessed the third server that
contained corporate financial data, the session was disconnected, and the administrator’s account
was disabled. Which activity triggered the behavior analytics tool?
Quiz
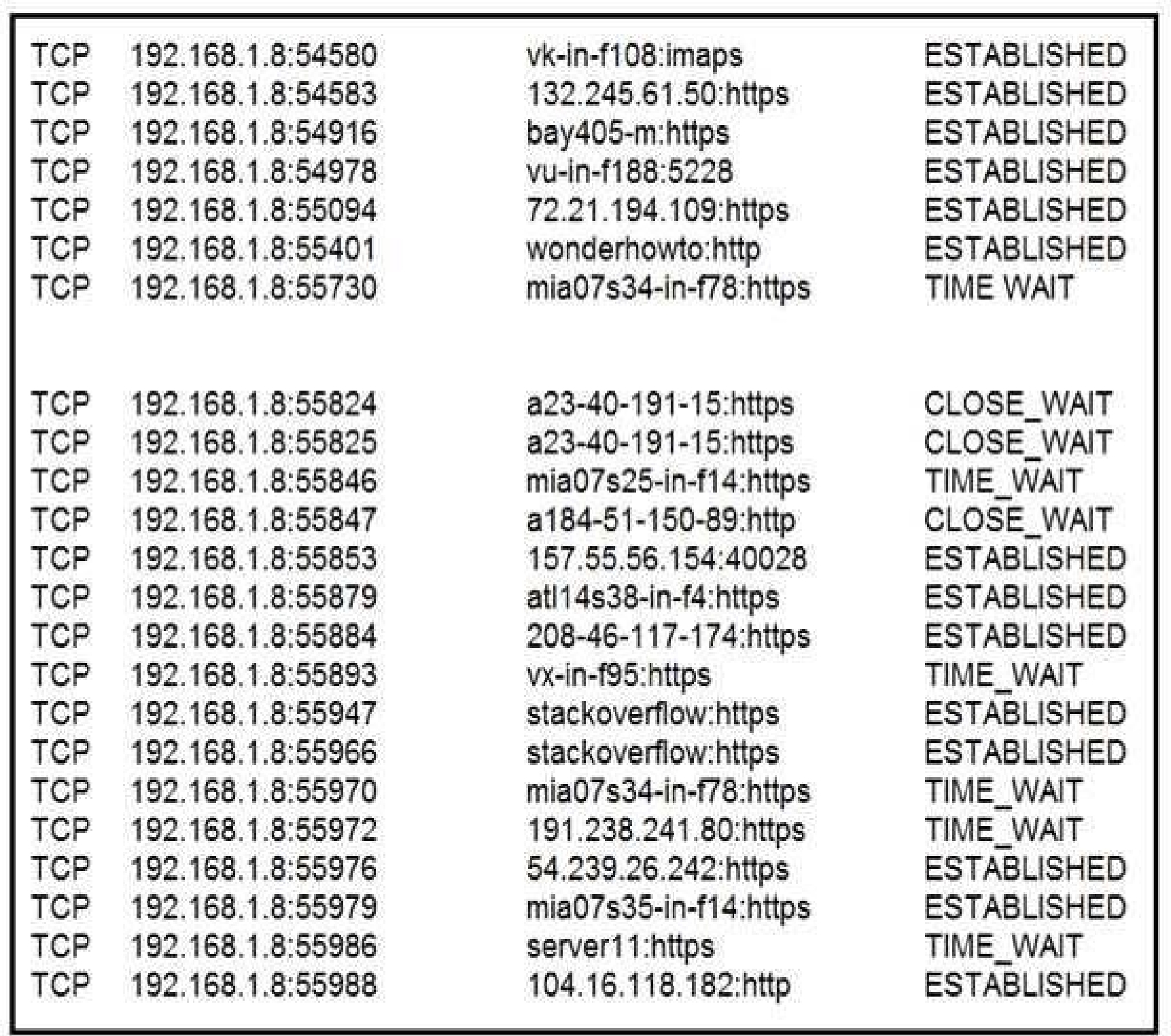
A security analyst needs to investigate a security incident involving several suspicious connections
with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?
Quiz
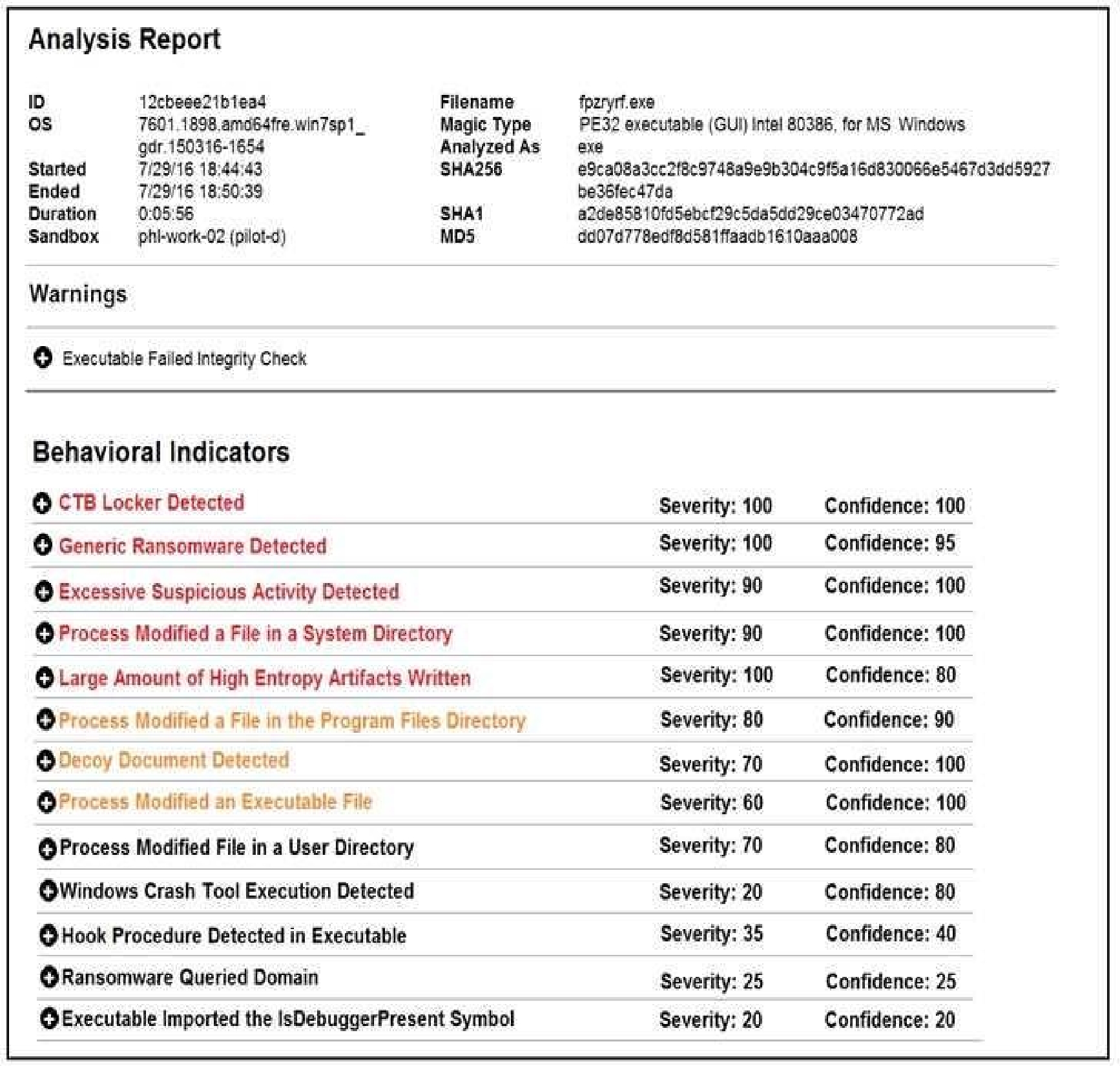
Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a
low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded
from this report?
Quiz
authorized individual to enter a secured premise. The incident was documented and given to a
security specialist to analyze. Which step should be taken at this stage?
Quiz
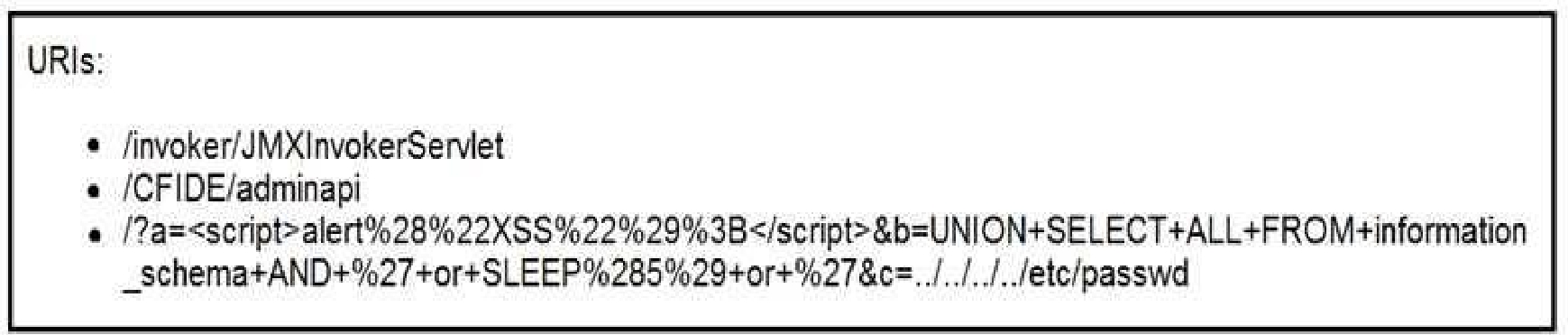
At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests
from known malicious Internet scanners?
Quiz
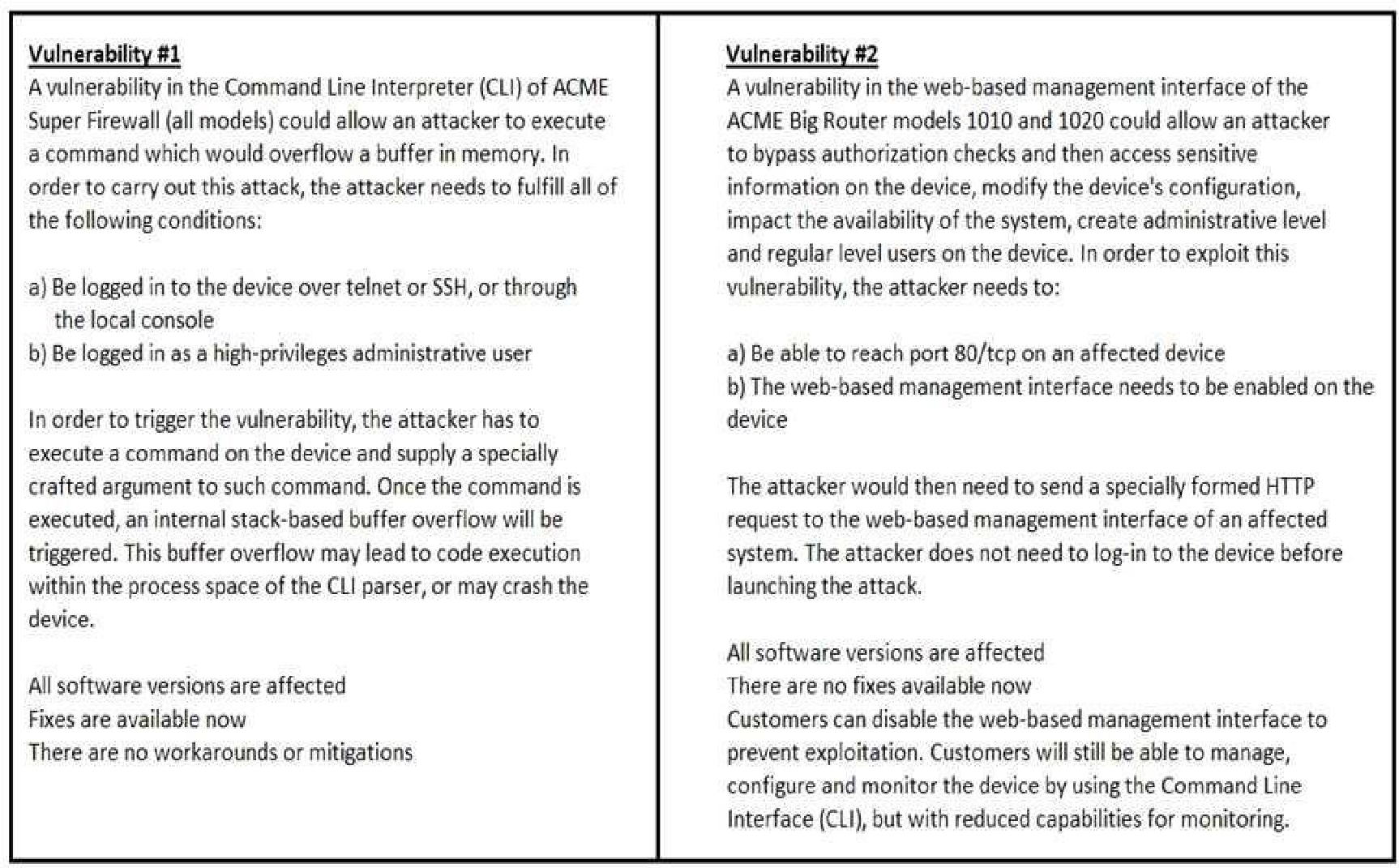
How must these advisories be prioritized for handling?
Quiz
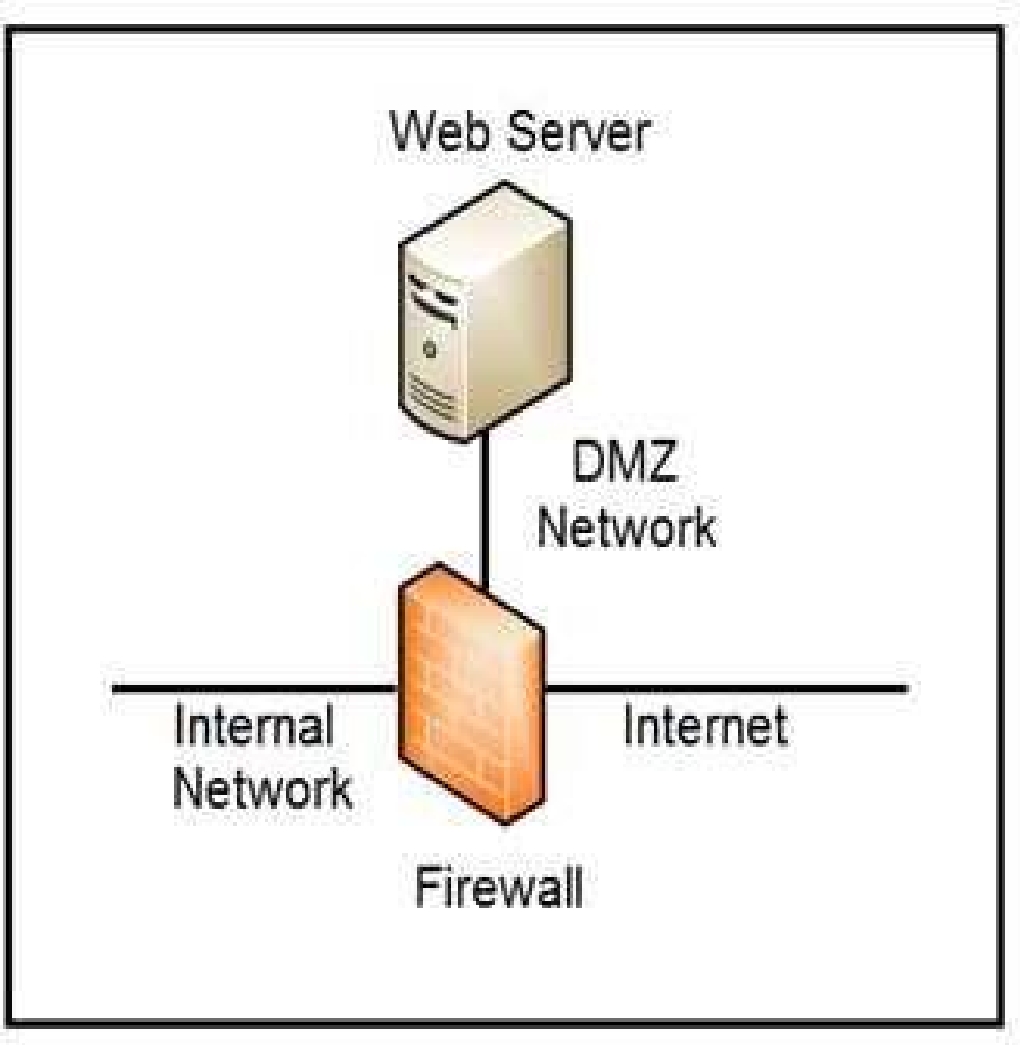
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
Performing CyberOps Using Core Security Technologies (CBRCOR) Practice test unlocks all online simulator questions
Thank you for choosing the free version of the Performing CyberOps Using Core Security Technologies (CBRCOR) practice test! Further deepen your knowledge on Cisco Simulator; by unlocking the full version of our Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator you will be able to take tests with over 139 constantly updated questions and easily pass your exam. 98% of people pass the exam in the first attempt after preparing with our 139 questions.
BUY NOWWhat to expect from our Performing CyberOps Using Core Security Technologies (CBRCOR) practice tests and how to prepare for any exam?
The Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator Practice Tests are part of the Cisco Database and are the best way to prepare for any Performing CyberOps Using Core Security Technologies (CBRCOR) exam. The Performing CyberOps Using Core Security Technologies (CBRCOR) practice tests consist of 139 questions and are written by experts to help you and prepare you to pass the exam on the first attempt. The Performing CyberOps Using Core Security Technologies (CBRCOR) database includes questions from previous and other exams, which means you will be able to practice simulating past and future questions. Preparation with Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator will also give you an idea of the time it will take to complete each section of the Performing CyberOps Using Core Security Technologies (CBRCOR) practice test . It is important to note that the Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator does not replace the classic Performing CyberOps Using Core Security Technologies (CBRCOR) study guides; however, the Simulator provides valuable insights into what to expect and how much work needs to be done to prepare for the Performing CyberOps Using Core Security Technologies (CBRCOR) exam.
BUY NOWPerforming CyberOps Using Core Security Technologies (CBRCOR) Practice test therefore represents an excellent tool to prepare for the actual exam together with our Cisco practice test . Our Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator will help you assess your level of preparation and understand your strengths and weaknesses. Below you can read all the quizzes you will find in our Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator and how our unique Performing CyberOps Using Core Security Technologies (CBRCOR) Database made up of real questions:
Info quiz:
- Quiz name:Performing CyberOps Using Core Security Technologies (CBRCOR)
- Total number of questions:139
- Number of questions for the test:50
- Pass score:80%
You can prepare for the Performing CyberOps Using Core Security Technologies (CBRCOR) exams with our mobile app. It is very easy to use and even works offline in case of network failure, with all the functions you need to study and practice with our Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator.
Use our Mobile App, available for both Android and iOS devices, with our Performing CyberOps Using Core Security Technologies (CBRCOR) Simulator . You can use it anywhere and always remember that our mobile app is free and available on all stores.
Our Mobile App contains all Performing CyberOps Using Core Security Technologies (CBRCOR) practice tests which consist of 139 questions and also provide study material to pass the final Performing CyberOps Using Core Security Technologies (CBRCOR) exam with guaranteed success. Our Performing CyberOps Using Core Security Technologies (CBRCOR) database contain hundreds of questions and Cisco Tests related to Performing CyberOps Using Core Security Technologies (CBRCOR) Exam. This way you can practice anywhere you want, even offline without the internet.
BUY NOW