Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
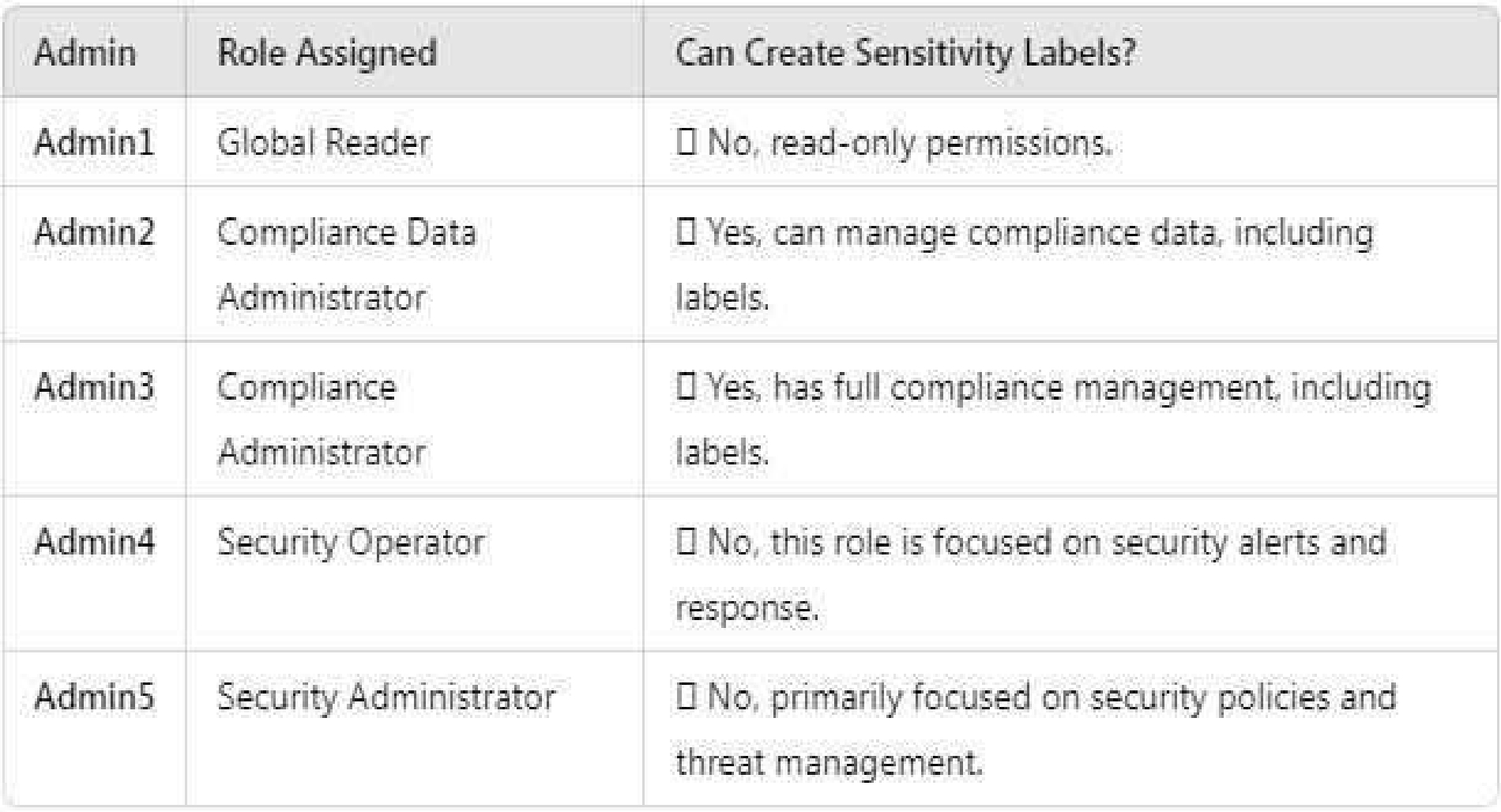
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.
Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
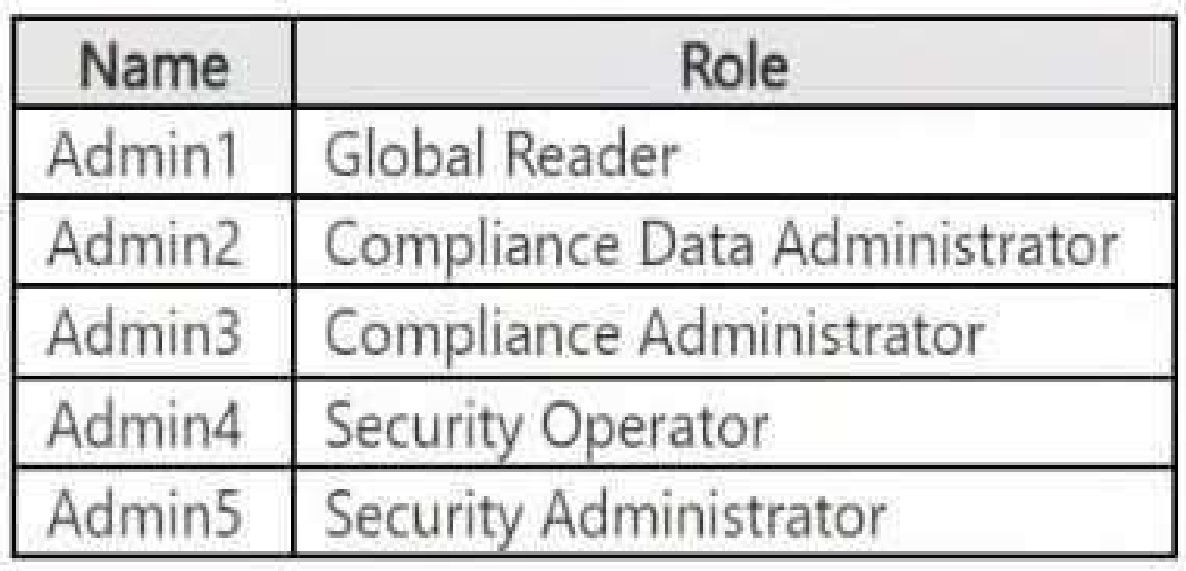
Site2 contains the files shown in the following table.
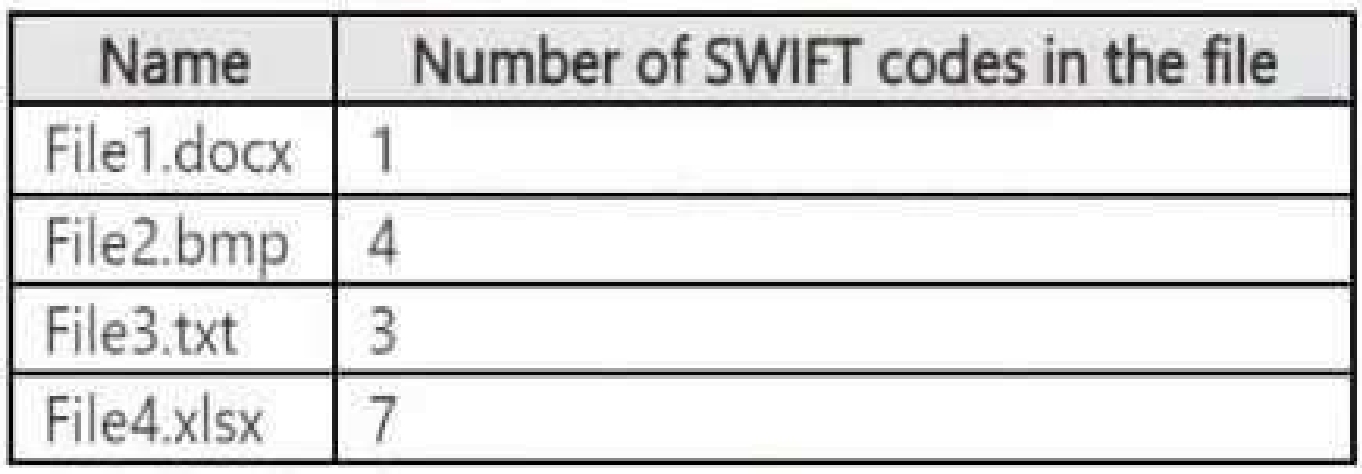
Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.
Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
To which user or users must you assign the Sensitivity Label Administrator role?
Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.

Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from
the list of actions to the answer area and arrange them in the correct order.
The goal is to automatically label documents in Site1 that contain credit card numbers. To achieve
this, we need a sensitivity label with an auto-labeling policy based on a sensitive info type that
detects credit card numbers.
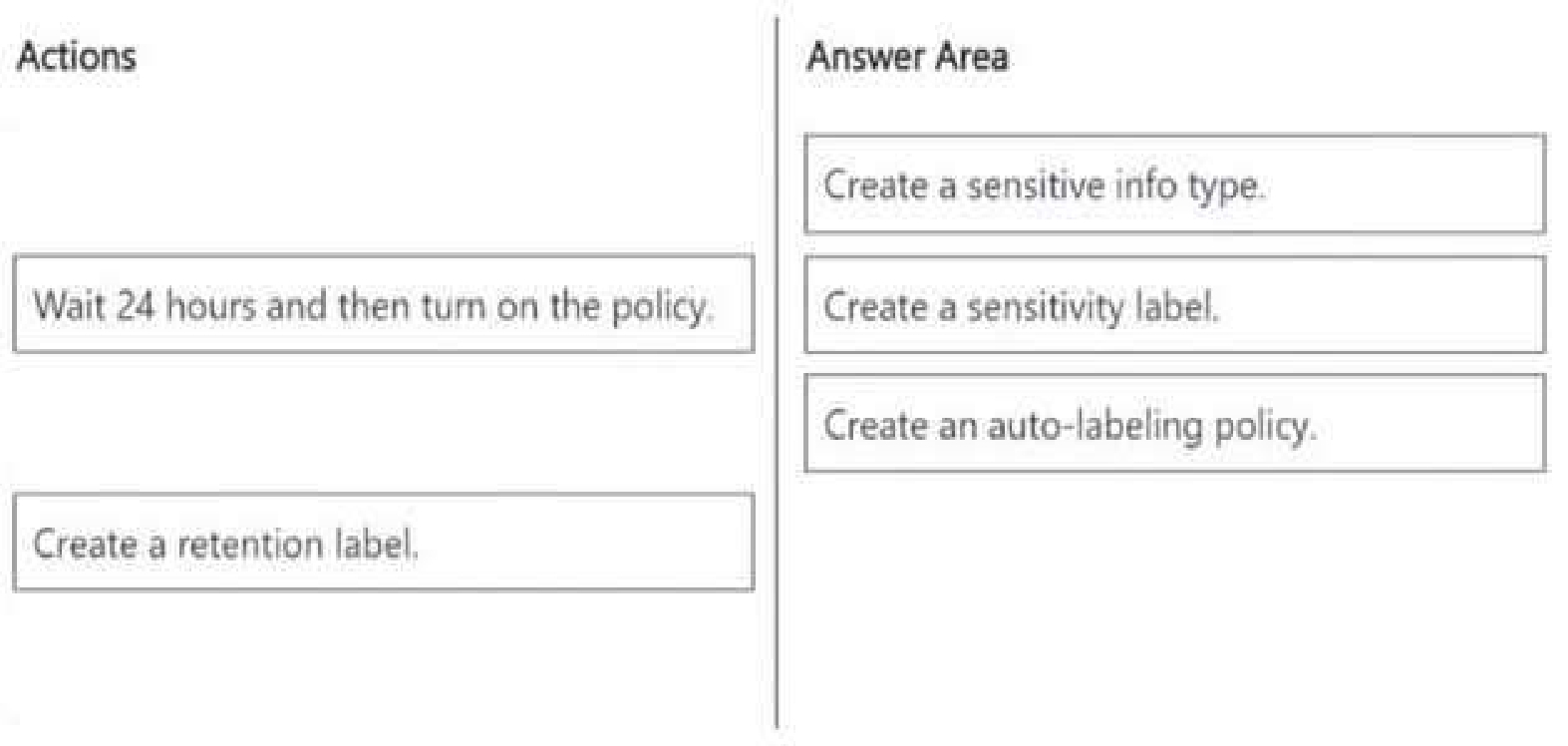
Step 1: Create a Sensitive Info Type
● A sensitive info type is needed to detect credit card numbers in documents.
● Microsoft Purview includes built-in sensitive info types for credit card numbers, but we can also
create a custom one if necessary.
Step 2: Create a Sensitivity Label
● A sensitivity label is required to classify and protect documents containing sensitive information.
● This label can apply encryption, watermarking, or access controls to credit card data.
Step 3: Create an Auto-Labeling Policy
● An auto-labeling policy ensures that the sensitivity label is applied automatically when credit card
numbers are detected in Site1.
● This policy is configured to scan files and automatically apply the correct sensitivity label.
Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.

Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
What should you create first, and what should you use for the detection method? To answer, select
the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
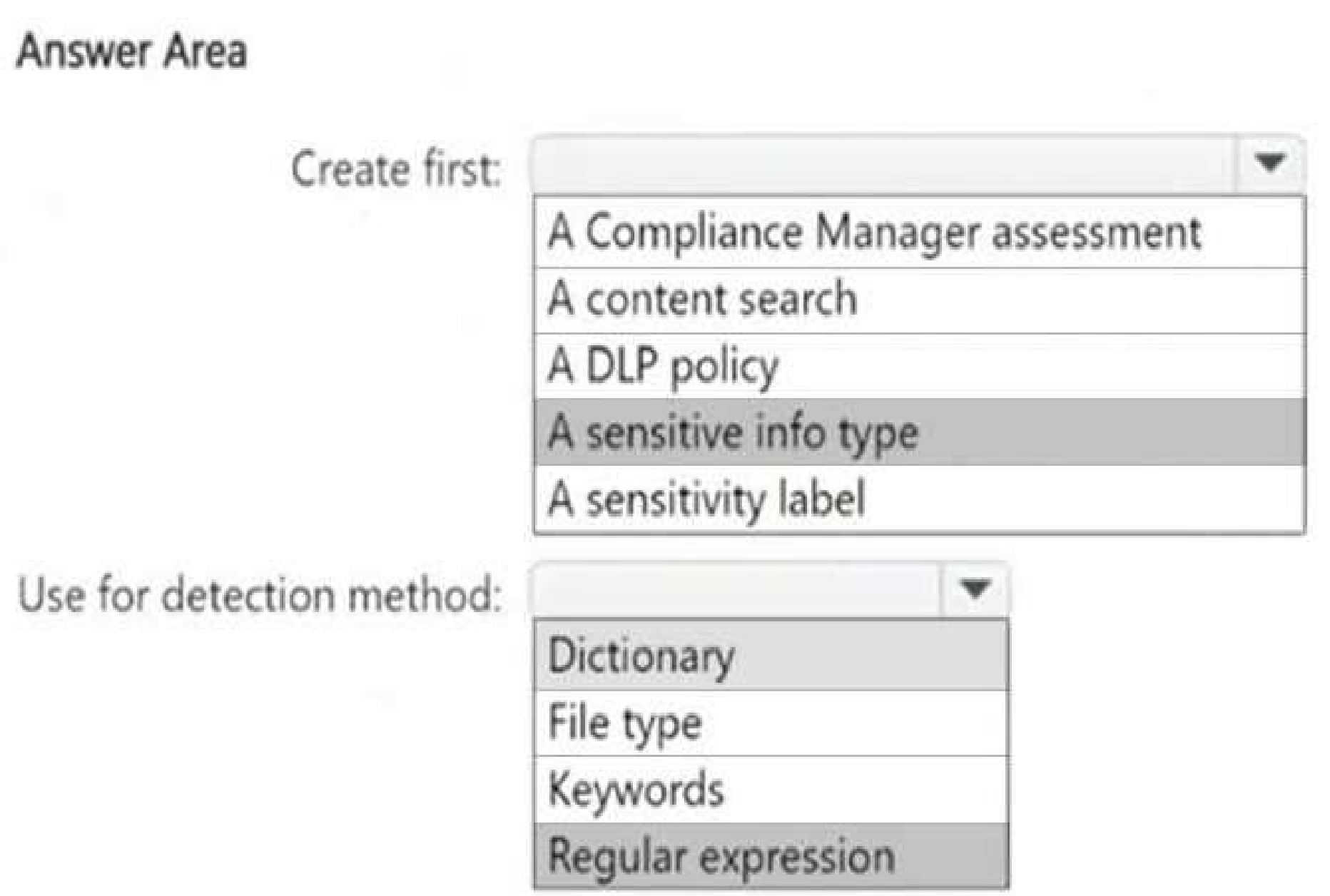
To detect and protect confidential documents, we need a custom rule to identify project codes that
start with 999 (since they are classified as confidential).
Box 1: A Sensitive Info Type (SIT) allows Microsoft Purview DLP policies to recognize structured data
(e.g., project codes). DLP policies require a sensitive info type to detect content based on patterns,
keywords, or dictionary terms. A sensitivity label alone does not define detection logic—it is used for
classification and protection after content is identified.
Box 2: Since project codes follow a structured 10-digit pattern, we should use a Regular Expression
(Regex) to match project codes that start with 999.
Example Regex pattern:
999\d{7}
This pattern detects a 10-digit number starting with "999".
Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.

Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
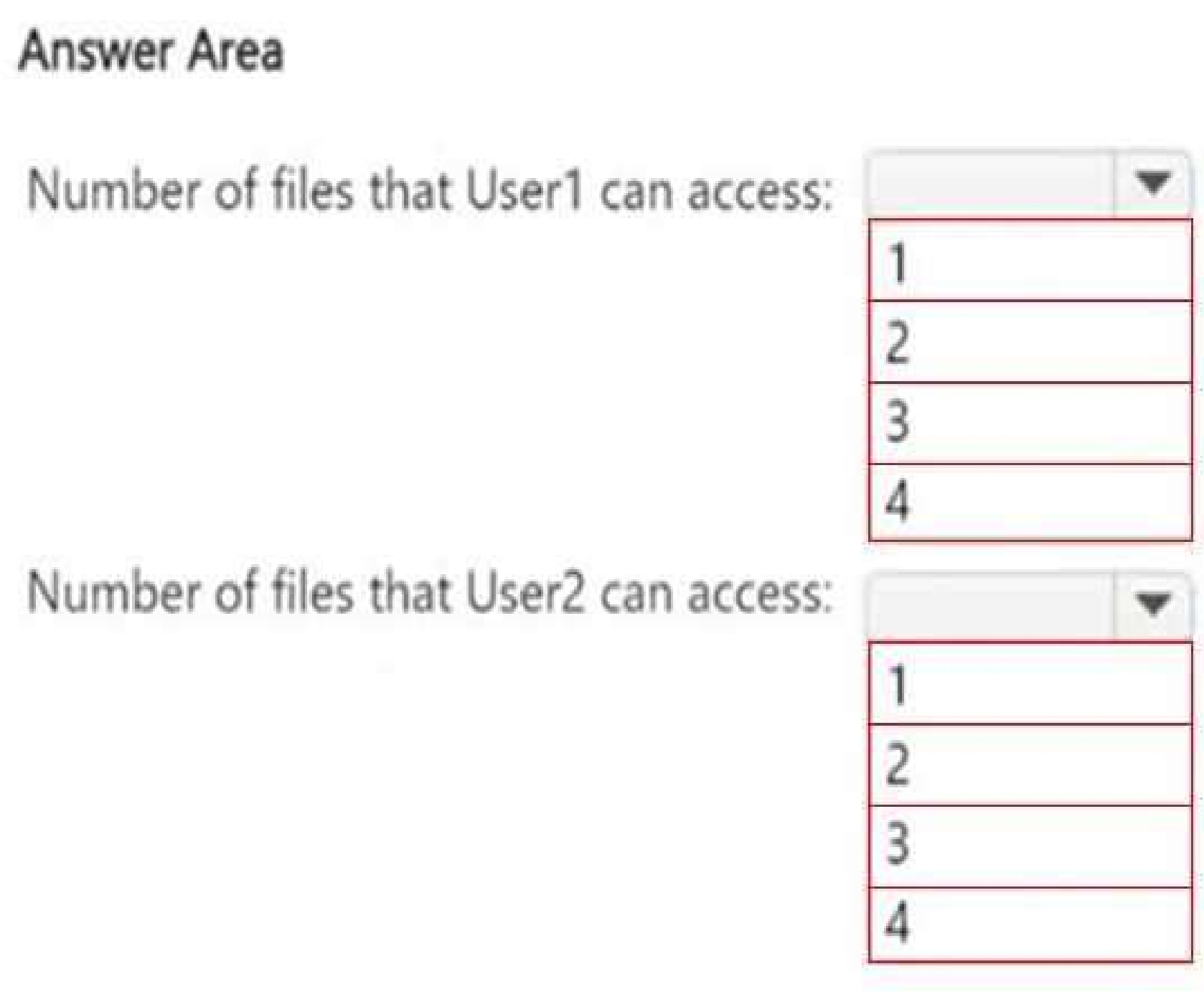
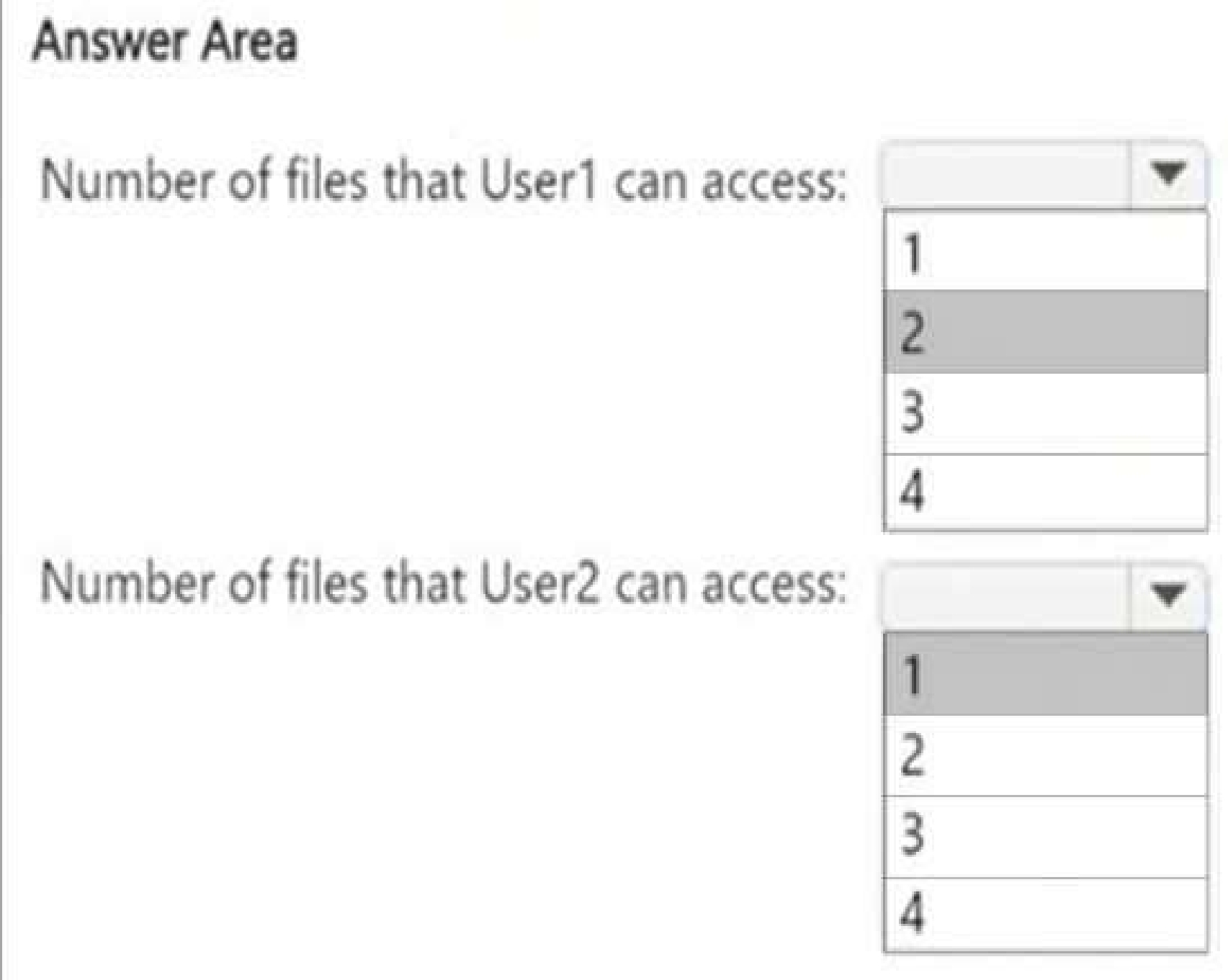
Understanding DLP Policy Impact on File Access
The DLP policy (DLPpolicy1) applies to Site2 and restricts access when:
● Content contains SWIFT Codes.
● Instance count is 2 or more.
File Analysis (Based on SWIFT Codes Count)
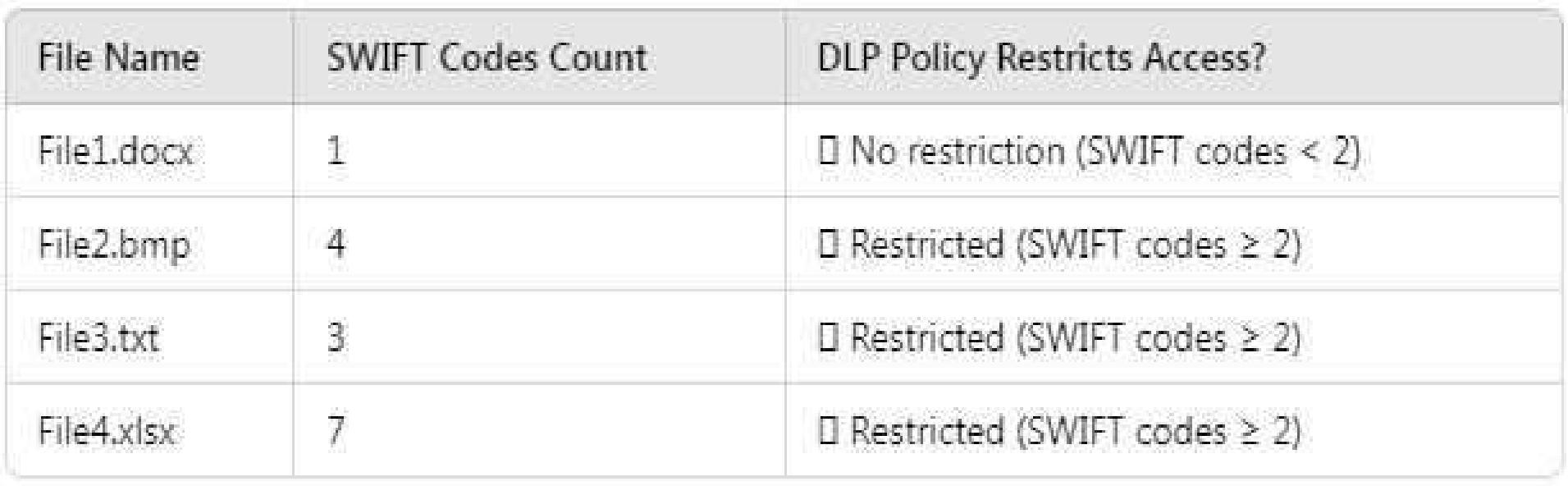
Files that remain accessible (not restricted by DLP):
● File1.docx (Contains only 1 SWIFT Code → Below restriction threshold)
User access after DLP policy is applied:
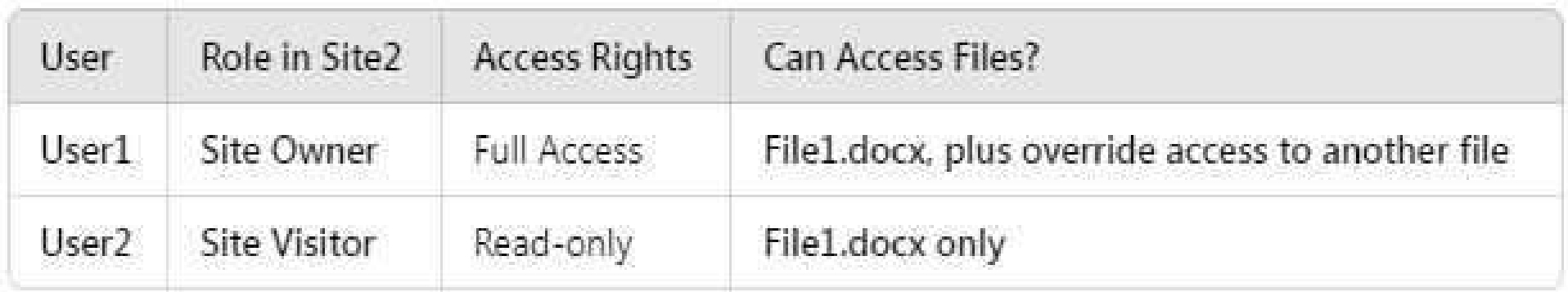
User1 (Site Owner):
● Has higher privileges and can override DLP restrictions (through admin intervention).
● Can access 2 files (File1.docx + override access to another file).
User2 (Site Visitor):
● Has read-only access but DLP blocks access to restricted files.
● Can only access 1 file (File1.docx), since all others are restricted.
Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.

Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
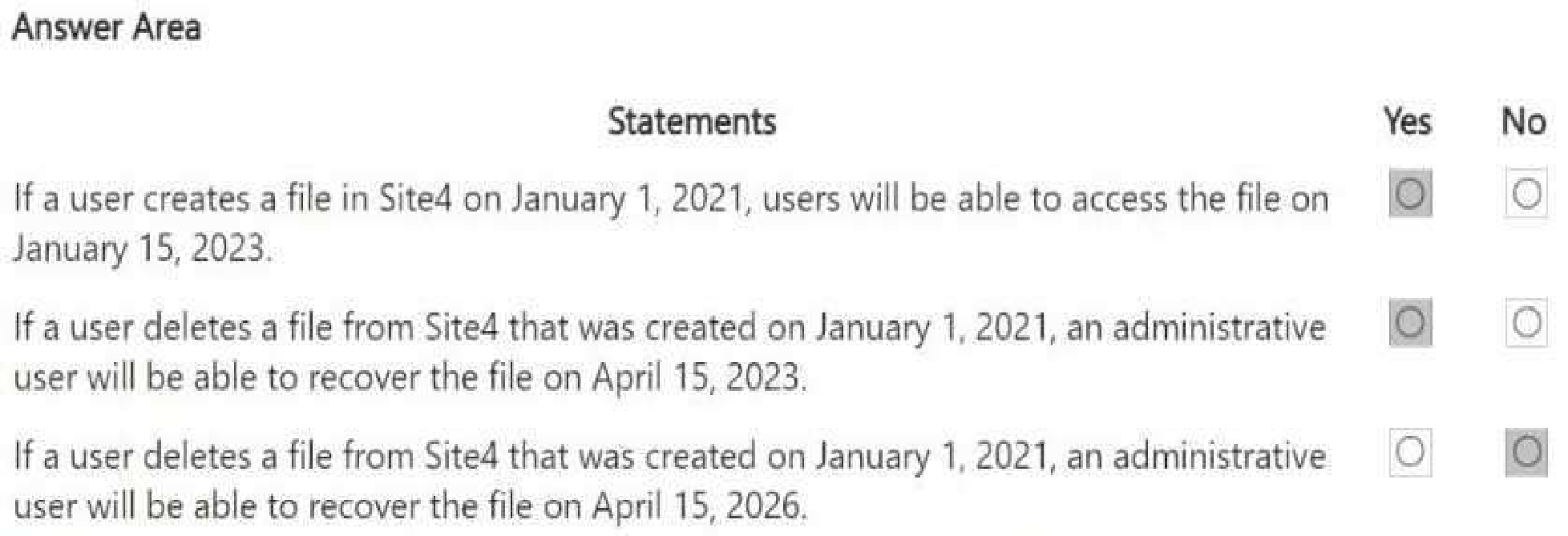
Understanding Site4's Retention Policies:
● Site4RetentionPolicy1 deletes items older than 2 years from creation. If a file was created on
January 1, 2021, it would be deleted after January 1, 2023.
● Site4RetentionPolicy2 retains files for 4 years from creation. If a file was created on January 1,
2021, it will be kept until January 1, 2025, but not deleted after that (policy states "Do nothing").
Statement 1 - Yes, because Site4RetentionPolicy2 ensures files are retained for 4 years.
Statement 2 - Yes, because Site4RetentionPolicy2 retains the file for 4 years (until January 1, 2025).
Statement 3 - No, because retention is only for 4 years (until January 1, 2025). After that, the policy
does "nothing," meaning the file is no longer recoverable after that period.
Quiz
Instructions
This is a case study. Case studies are not timed separately from other exam sections. You can use as
much exam time as you would like to complete each case study. However, there might be additional
case studies or other exam sections. Manage your time to ensure that you can complete all the exam
sections in the time provided. Pay attention to the Exam Progress at the top of the screen so you
have sufficient time to complete any exam sections that follow this case study.
To answer the case study questions, you will need to reference information that is provided in the
case. Case studies and associated questions might contain exhibits or other resources that provide
more information about the scenario described in the case. Information provided in an individual
question does not apply to the other questions in the case study.
A Review Screen will appear at the end of this case study. From the Review Screen, you can review
and change your answers before you move to the next exam section. After you leave this case study,
you will NOT be able to return to it.
To start the case study
To display the first question in this case study, select the "Next" button. To the left of the question, a
menu provides links to information such as business requirements, the existing environment, and
problem statements. Please read through all this information before answering any questions. When
you are ready to answer a question, select the "Question" button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in
Seattle, Boston, and Johannesburg.
Existing Environment
Microsoft 365 Environment
Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown
in the following table.

Users store data in the following locations:
● SharePoint sites
● OneDrive accounts
● Exchange email
● Exchange public folders
● Teams chats
● Teams channel messages
When users in the research department create documents, they must add a 10-digit project code to
each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
Site2 contains the files shown in the following table.

Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.

Site3 stores documents related to the company's projects. The documents are organized in a folder
hierarchy based on the project.
Site4 has the following two retention policies applied:
● Name: Site4RetentionPolicy1
● Locations to apply the policy: Site4
● Delete items older than: 2 years
● Delete content based on: When items were created
● Name: Site4RetentionPolicy2
● Locations to apply the policy: Site4
● Retain items for a specific period: 4 years
● Start the retention period based on: When items were created
● At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research
department documents were leaked.
Requirements
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
● Name: DLPpolicy1
● Locations to apply the policy: Site2
● Conditions:
● Content contains any of these sensitive info types: SWIFT Code
● Instance count: 2 to any
● Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
● All administrative users must be able to review DLP reports.
● Whenever possible, the principle of least privilege must be used.
● For all users, all Microsoft 365 data must be retained for at least one year.
● Confidential documents must be detected and protected by using Microsoft 365.
● Site1 documents that include credit card numbers must be labeled automatically.
● All administrative users must be able to create Microsoft 365 sensitivity labels.
● After a project is complete, the documents in Site3 that relate to the project must be retained for
10 years.
What is the minimum number of retention policies required to achieve the goal?
Quiz
Channel1 contains research and development documents.
You plan to implement Microsoft 365 Copilot for the subscription.
You need to prevent the contents of files stored in Channel1 from being included in answers
generated by Copilot and shown to unauthorized users.
What should you use?
Quiz
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You plan to deploy a Defender for Cloud Apps file policy that will be triggered when the following
conditions are met:
● A file is shared externally.
● A file is labeled as internal only.
Which filter should you use for each condition? To answer, drag the appropriate filters to the correct
conditions. Each filter may be used once, more than once, or not at all. You may need to drag the
split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.


Quiz
You create the sensitivity labels shown in the following table.
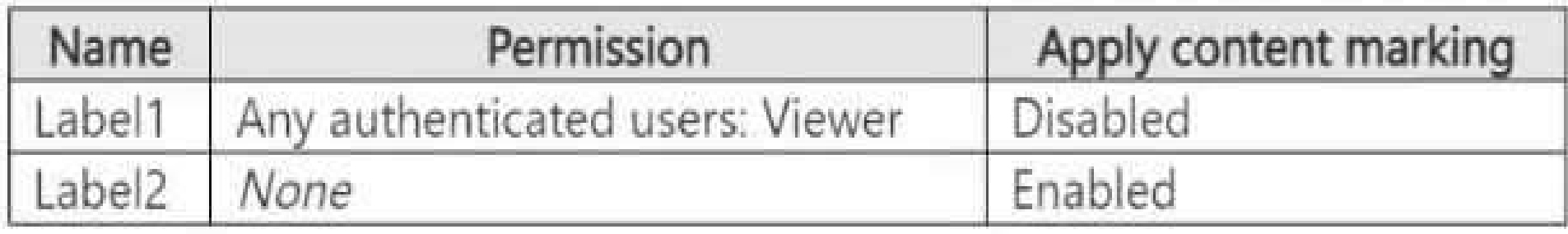
You apply the labels to the files as shown in the following table.
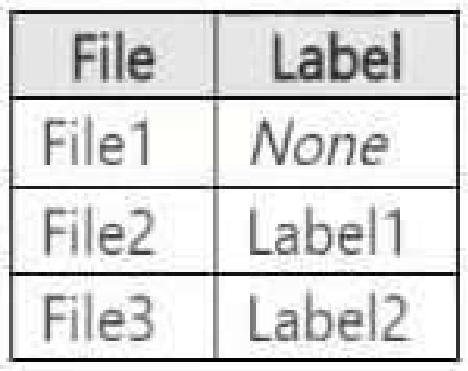
You ask Microsoft 365 Copilot to summarize the files, and you receive the results shown in the
following table.
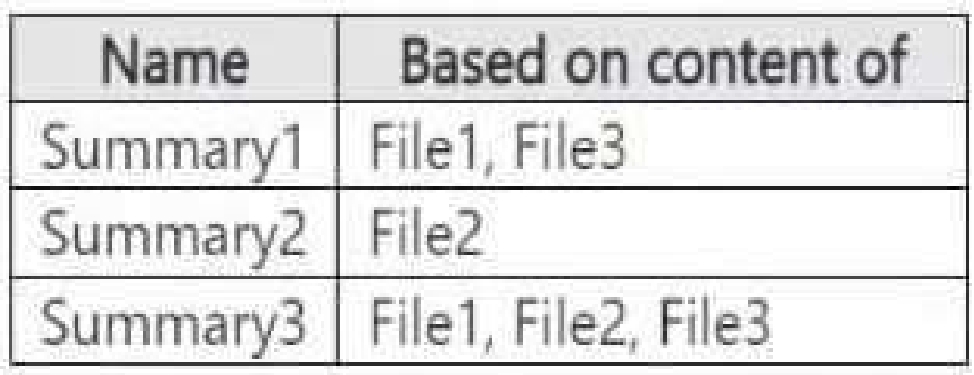
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Quiz
You need to create a sensitivity label named Label1. The solution must ensure that users can use
Microsoft 365 Copilot to summarize files that have Label1 applied.
Which permission should you select for Label1?
Microsoft Administering Information Security in Microsoft 365 Practice test unlocks all online simulator questions
Thank you for choosing the free version of the Microsoft Administering Information Security in Microsoft 365 practice test! Further deepen your knowledge on Microsoft Simulator; by unlocking the full version of our Microsoft Administering Information Security in Microsoft 365 Simulator you will be able to take tests with over 178 constantly updated questions and easily pass your exam. 98% of people pass the exam in the first attempt after preparing with our 178 questions.
BUY NOWWhat to expect from our Microsoft Administering Information Security in Microsoft 365 practice tests and how to prepare for any exam?
The Microsoft Administering Information Security in Microsoft 365 Simulator Practice Tests are part of the Microsoft Database and are the best way to prepare for any Microsoft Administering Information Security in Microsoft 365 exam. The Microsoft Administering Information Security in Microsoft 365 practice tests consist of 178 questions and are written by experts to help you and prepare you to pass the exam on the first attempt. The Microsoft Administering Information Security in Microsoft 365 database includes questions from previous and other exams, which means you will be able to practice simulating past and future questions. Preparation with Microsoft Administering Information Security in Microsoft 365 Simulator will also give you an idea of the time it will take to complete each section of the Microsoft Administering Information Security in Microsoft 365 practice test . It is important to note that the Microsoft Administering Information Security in Microsoft 365 Simulator does not replace the classic Microsoft Administering Information Security in Microsoft 365 study guides; however, the Simulator provides valuable insights into what to expect and how much work needs to be done to prepare for the Microsoft Administering Information Security in Microsoft 365 exam.
BUY NOWMicrosoft Administering Information Security in Microsoft 365 Practice test therefore represents an excellent tool to prepare for the actual exam together with our Microsoft practice test . Our Microsoft Administering Information Security in Microsoft 365 Simulator will help you assess your level of preparation and understand your strengths and weaknesses. Below you can read all the quizzes you will find in our Microsoft Administering Information Security in Microsoft 365 Simulator and how our unique Microsoft Administering Information Security in Microsoft 365 Database made up of real questions:
Info quiz:
- Quiz name:Microsoft Administering Information Security in Microsoft 365
- Total number of questions:178
- Number of questions for the test:50
- Pass score:80%
You can prepare for the Microsoft Administering Information Security in Microsoft 365 exams with our mobile app. It is very easy to use and even works offline in case of network failure, with all the functions you need to study and practice with our Microsoft Administering Information Security in Microsoft 365 Simulator.
Use our Mobile App, available for both Android and iOS devices, with our Microsoft Administering Information Security in Microsoft 365 Simulator . You can use it anywhere and always remember that our mobile app is free and available on all stores.
Our Mobile App contains all Microsoft Administering Information Security in Microsoft 365 practice tests which consist of 178 questions and also provide study material to pass the final Microsoft Administering Information Security in Microsoft 365 exam with guaranteed success. Our Microsoft Administering Information Security in Microsoft 365 database contain hundreds of questions and Microsoft Tests related to Microsoft Administering Information Security in Microsoft 365 Exam. This way you can practice anywhere you want, even offline without the internet.
BUY NOW