Quiz
Quiz
Spoofing attacks?
Quiz
create or alter SQL commands to gain access to private data or execute commands in the database.
What technique does Jimmy use to compromise a database?
system
users from gaining access
privilege of the database
target system
Quiz
the IDS will not spot the true nature of the fully assembled datagram. The datagram is not
reassembled until it reaches its final destination. It would be a processor-intensive task for IDS to
reassemble all fragments itself, and on a busy system the packet will slip through the IDS onto the
network. What is this technique called?
Quiz
business, they just have to find a job opening, prepare someone to pass the interview, have that
person hired, and they will be in the organization.

How would you prevent such type of attacks?
Quiz
are not able to detect what the packets intends to do.
Quiz
order to find some information about the target they are attempting to penetrate. How would you
call this type of activity?
Quiz
disclosure. An anonymizer protects all of your computer's identifying information while it surfs for
you, enabling you to remain at least one step removed from the sites you visit. You can visit Web
sites without allowing anyone to gather information on sites visited by you. Services that provide
anonymity disable pop-up windows and cookies, and conceal visitor's IP address. These services
typically use a proxy server to process each HTTP request. When the user requests a Web page by
clicking a hyperlink or typing a URL into their browser, the service retrieves and displays the
information using its own server. The remote server (where the requested Web page resides)
receives information on the anonymous Web surfing service in place of your information. In which
situations would you want to use anonymizer? (Select 3 answers)
want to visit.
Quiz
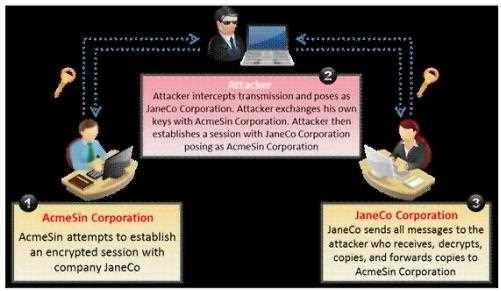
Quiz
recipe. Jack calls Jane, an accountant at Brown Co., pretending to be an administrator from Brown
Co. Jack tells Jane that there has been a problem with some accounts and asks her to verify her
password with him ''just to double check our records.'' Jane does not suspect anything amiss, and
parts with her password. Jack can now access Brown Co.'s computers with a valid user name and
password, to steal the cookie recipe. What kind of attack is being illustrated here?
GAQM Certified Professional Ethical Hacker (CPEH) Practice test unlocks all online simulator questions
Thank you for choosing the free version of the GAQM Certified Professional Ethical Hacker (CPEH) practice test! Further deepen your knowledge on GAQM Simulator; by unlocking the full version of our GAQM Certified Professional Ethical Hacker (CPEH) Simulator you will be able to take tests with over 873 constantly updated questions and easily pass your exam. 98% of people pass the exam in the first attempt after preparing with our 873 questions.
BUY NOWWhat to expect from our GAQM Certified Professional Ethical Hacker (CPEH) practice tests and how to prepare for any exam?
The GAQM Certified Professional Ethical Hacker (CPEH) Simulator Practice Tests are part of the GAQM Database and are the best way to prepare for any GAQM Certified Professional Ethical Hacker (CPEH) exam. The GAQM Certified Professional Ethical Hacker (CPEH) practice tests consist of 873 questions and are written by experts to help you and prepare you to pass the exam on the first attempt. The GAQM Certified Professional Ethical Hacker (CPEH) database includes questions from previous and other exams, which means you will be able to practice simulating past and future questions. Preparation with GAQM Certified Professional Ethical Hacker (CPEH) Simulator will also give you an idea of the time it will take to complete each section of the GAQM Certified Professional Ethical Hacker (CPEH) practice test . It is important to note that the GAQM Certified Professional Ethical Hacker (CPEH) Simulator does not replace the classic GAQM Certified Professional Ethical Hacker (CPEH) study guides; however, the Simulator provides valuable insights into what to expect and how much work needs to be done to prepare for the GAQM Certified Professional Ethical Hacker (CPEH) exam.
BUY NOWGAQM Certified Professional Ethical Hacker (CPEH) Practice test therefore represents an excellent tool to prepare for the actual exam together with our GAQM practice test . Our GAQM Certified Professional Ethical Hacker (CPEH) Simulator will help you assess your level of preparation and understand your strengths and weaknesses. Below you can read all the quizzes you will find in our GAQM Certified Professional Ethical Hacker (CPEH) Simulator and how our unique GAQM Certified Professional Ethical Hacker (CPEH) Database made up of real questions:
Info quiz:
- Quiz name:GAQM Certified Professional Ethical Hacker (CPEH)
- Total number of questions:873
- Number of questions for the test:50
- Pass score:80%
You can prepare for the GAQM Certified Professional Ethical Hacker (CPEH) exams with our mobile app. It is very easy to use and even works offline in case of network failure, with all the functions you need to study and practice with our GAQM Certified Professional Ethical Hacker (CPEH) Simulator.
Use our Mobile App, available for both Android and iOS devices, with our GAQM Certified Professional Ethical Hacker (CPEH) Simulator . You can use it anywhere and always remember that our mobile app is free and available on all stores.
Our Mobile App contains all GAQM Certified Professional Ethical Hacker (CPEH) practice tests which consist of 873 questions and also provide study material to pass the final GAQM Certified Professional Ethical Hacker (CPEH) exam with guaranteed success. Our GAQM Certified Professional Ethical Hacker (CPEH) database contain hundreds of questions and GAQM Tests related to GAQM Certified Professional Ethical Hacker (CPEH) Exam. This way you can practice anywhere you want, even offline without the internet.
BUY NOW